Last July, a security firm discovered cybercriminals had stolen a casino's data by hacking into one of its aquariums. The aquarium's low-security internet-connected thermostat gave hackers a foothold in the casino's network. Once there, they accessed the high-roller database and pulled that data back out from the thermostat and up to the cloud.
Businesses are integrating IoT devices into every area of operation-from factory floor sensors that detect vibrations to desks that automatically alert employees to take a break from sitting. IoT could soon be as much a part of corporate IT infrastructure as PCs.
However, in a rush to adopt this next iteration of digital transformation, companies are forgetting to consult their CISOs. As IoT connects physical with cyber, companies' digital footprints are expanding exponentially, providing more and more vulnerabilities for attackers to exploit. A survey found that almost 20% of organizations had at least one IoT-related attack in the past three years.
Stripped down for performance, not security
By design, IoT devices have little memory-typically too little for security add-ons. The demands of mobility, extended battery life, and price margins keep IoT sensors lean but defenseless.
That isn't all. IoT software rarely allows for automatic patches, which goes against cybersecurity's first commandment: patch immediately. This was the harsh reality learned by victims of 2017's WannaCry ransomware attack, which infected organizations that lacked an available software patch. IoT devices may also have pre-loaded, unchangeable passwords-a vulnerability 2016's massive Mirai botnet exploited by scanning for IoT devices that were still set to factory-default login information. Just one well-known vulnerability, called DNS rebinding, is estimated to affect half a billion IoT devices in businesses. A sampling of IoT devices found 83% hadn't yet patched against known threats.
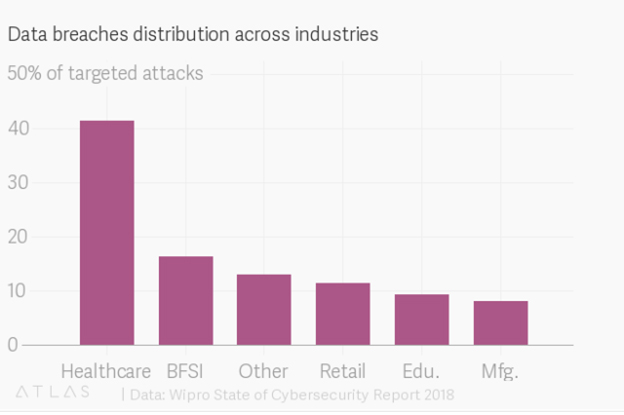
The multitude of IoT devices, running a multitude of software platforms, complicates CISOs' jobs and should raise alarm with CEOs. An attack via IoT could be catastrophic, according to 97% of firms surveyed. The healthcare industry is especially at risk, finishing as 2017's biggest victim of data breaches. While in 2016 30% of the attacks targeted the healthcare industry, in 2017 the number jumped to 41%. That percentage is likely to continue rising as healthcare IoT expands. A report by Allied Market Research predicts that the IoT healthcare market will reach $136.8 billion worldwide by 2021.
So what's a CISO to do? Here's some good news: 74% of organizations have IoT security assessment controls in place already, and just over 60% of organizations have password protected their IoT devices.
But the scale of the IoT security challenge requires an additional two-tiered approach: automate and institutionalize. The former assures fast and routine controls across thousands of tiny IoT sensors. The latter curtails risks from the get-go and ensures CISOs can develop their tools as hacking gets more sophisticated.
Automation: fighting botnets with bots
Automated security takes several forms. Automated platforms can look for "Indicators of Compromise," check VPNs, and detect and shut down intrusions in progress. Using artificial intelligence, automated security platforms can spot abnormal activity-the rogue fish tank was uncovered because it was the casino's only device sending data to Finland. The number of companies using "Security Orchestration, Automation, and Response" tools is expected to jump to 15% in 2020, from 1% in 2017.
New security automation solutions will be able to "speak" to IoT devices, even very simple ones like CCTV cameras or biometric sensors. This is important, considering the incredible variety of IoT devices, and the fact that they often are deployed in large numbers. Automated software is being developed that could reach out and patch any device as soon as a vulnerability is discovered. One example, called Mayhem, won a Pentagon contest to create automated patching.
In the meantime, machine authentication verifies any device connecting to your network at a more sophisticated level than simply username and password, instead using a digital certificate that will stop your thermostat from talking to a hacker.
Getting security into the institution's DNA
But automation isn't enough. IoT should undergo the same due diligence that any IT infrastructure gets. A building supervisor installing a smart electronic key system, a product engineer choosing IoT components, or a casino manager adding a smart thermometer to a fish tank today are not likely to ponder over the security of their selections. Those decisions should be made under a CISO's institutionalized supervision. To ensure technological advances don't introduce security flaws, CISOs and their tools should be part of purchasing, designing, or implementing all technological transformations, including IoT.
This requires a paradigmatic shift in the CISOs' role; they shouldn't be siloed within an organization, but rather should be involved in all aspects of an institution-from employee training to vendor selection. The lack of standardization in innovative hardware and software like IoT means that security especially needs to be baked in from the moment a company even considers adding sensors or smart devices-before any purchase is made.
Integrating security from the beginning also keeps security from being seen as a hindrance to innovation. As more smart lights, smart cameras, smart printers, and smart aquariums are compromised, people will see that what's really smart is to make sure connected devices are secure from the start.
It's one thing to adopt innovative technology. It's another to deploy that technology smartly and safely.