As they refine and redefine their cybersecurity strategies and pursue digital transformation, banking and finance enterprises should consider the importance of an integrated architecture to transform their cybersecurity environment. Zero-trust security, in particular, is proving itself to be a holistic, practical and adaptable solution to the cybersecurity challenges that banking and finance enterprises now face. Even for organizations that have already adopted zero-trust, this is a moment to step back and reconsider the potential gaps in the enterprise’s zero-trust cybersecurity estate.
The move to remote work at the outset of the pandemic created instantaneous cybersecurity risks for the banking and finance industries. A cybersecurity strategy could no longer rely mostly on the defined network perimeter of a large office. Instead, companies were forced to trade their traditional security architectures for ecosystems that allowed employees to access cloud services from anywhere.
Most enterprises handled the situation using temporary cybersecurity fixes. However, it is now abundantly clear that remote and hybrid work are here to stay, and companies must convert ad-hoc remote/hybrid cybersecurity strategies into durable strategies for the new reality.
As they refine and redefine their cybersecurity strategies, banking and finance enterprises should consider the importance of an integrated architecture to transform their cybersecurity environment. Zero-trust security, in particular, is proving itself to be a holistic, practical and adaptable solution to the cybersecurity challenges that banking and finance enterprises now face. Even for organizations that have already adopted zero-trust, this is a moment to step back and reconsider the potential gaps in the enterprise’s zero-trust cybersecurity estate.
Cyber security strategy using zero-trust
Verizon’s most recent Data Breach Investigation Report states that external threats currently account for 73% of all data breaches in finance and insurance companies. Most external data breaches take advantage of a lack of internal control mechanisms, which allows for unhindered lateral movement of malware in the network. The other 27% of breaches are internal. In these cases, the employee enabling the data breach has legitimate reasons to access company data and applications. However, in the case of a threat, they are using the network or accessing the data in a way that goes far beyond their business function. In both cases, the problem is that bad actors can navigate through IT systems with very little friction or visibility.
A zero-trust approach to cybersecurity aims to solve the problem of wide-open, un-policed internal IT systems. Zero-trust, first coined by Forrester more than a decade ago, takes into account information about data, networks, people, workloads and devices (see Figure 1). This strategy leverages analytics and automation to provide visibility and access based on a trust-but-verify approach. The goal is to protect sensitive data and information while also providing access to users based on legitimate business needs. As such, zero-trust is becoming a vital cybersecurity framework for organizations that rely on significant amounts of sensitive or private information. Because this approach responds to an organization’s unique data types, management structure and networks/devices, it can be adapted and fine-tuned based on the business priorities of a given enterprise.
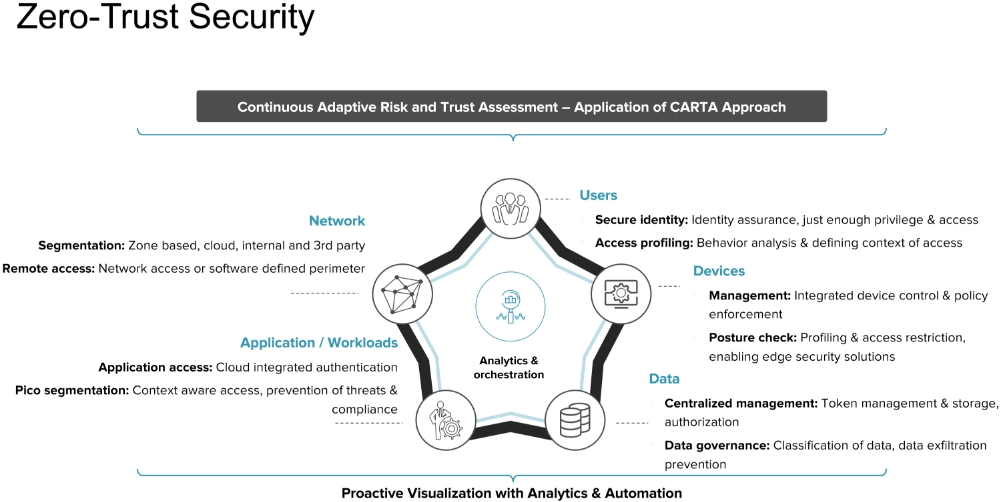
Figure 1: Five elements of zero trust security and use cases
Zero-trust security for the banking & finance industry
Wipro provides a holistic approach to zero-trust security, leveraging a framework and a working model that relies on a comprehensive range of security tools and functionalities while also integrating elements of cybersecurity controls. This approach helps enterprises adopt zero-trust security seamlessly, using specific process-driven security toolsets to define and control various levels of access to organizational resources.
For example, in one client engagement with a large private bank, we employed zero-trust security to both strengthen the security architecture and adhere to regulatory mandates. We assessed the entire network and controls, recommended changes in the security architecture based on application data flow and user access, and strengthened security controls for the “crown jewel” applications. The result: improved remote access for users combined with a reduction in attack surface.
Wipro leverages a zero-trust framework (Figure 2) derived from the Forrester ZTX framework and other industry standards. This framework follows the National Institute of Standards and Technology (NIST) approach, but expands further to an adaptable architecture.
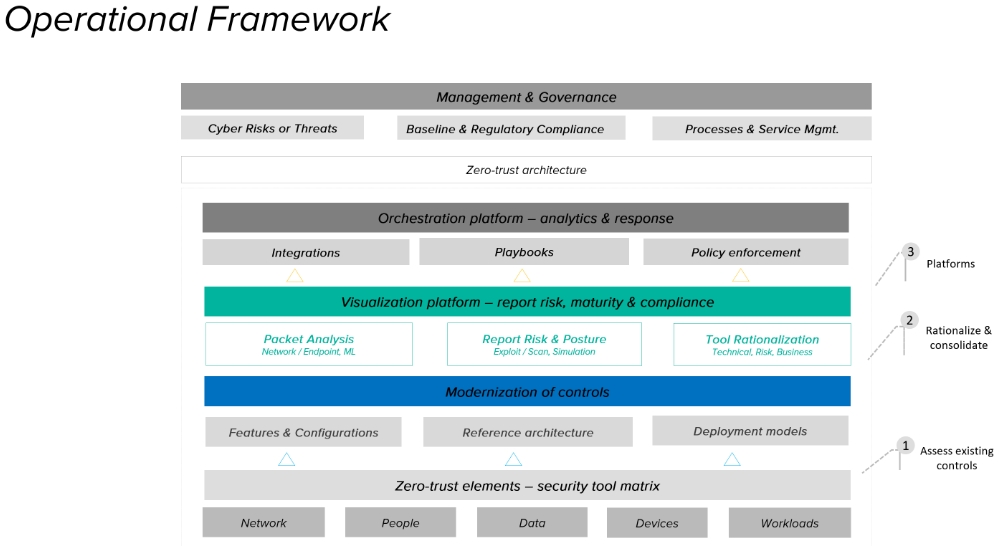
Figure 2: Wipro’s Operational Framework of Zero-trust Security
Multiple security products with zero-trust capabilities can contribute as building blocks of the overall solution. The centralized platform enables visibility of an entire security estate and identifies potential security risks, driving constant monitoring that continuously improves the security posture.
A truly mature cybersecurity architecture is fully interconnected; any anomaly in the system can trigger changes in the levels of access.
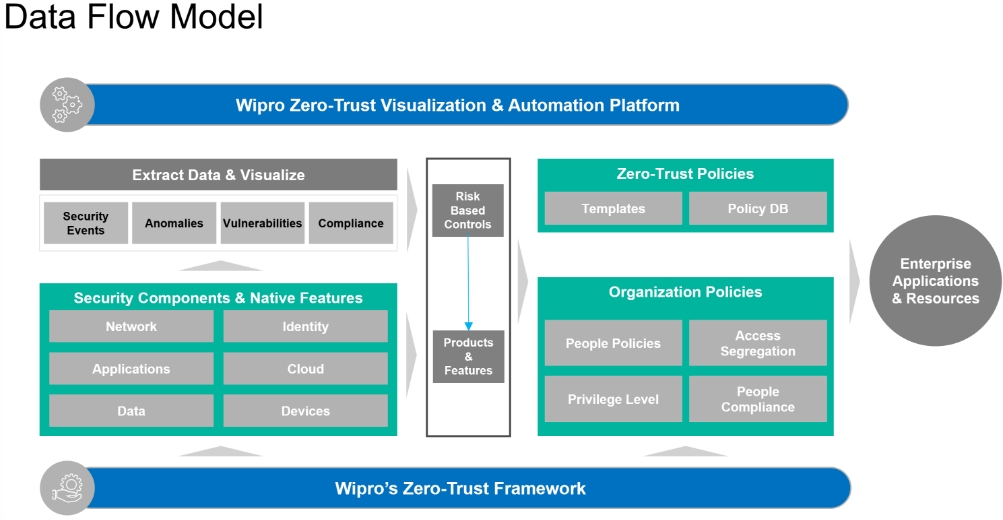
Figure 3: Data flow of zero trust security architecture
Wipro’s approach to zero-trust
Leveraging our zero-trust framework, Wipro assesses the enterprise environment’s current cybersecurity maturity, rationalizes its security tools and strengthens the controls to creates a cohesive architecture with the appropriate ecosystem of security tools. (See Figure 4 for more context on the five zero-trust capability levels that inform our maturity assessment.)
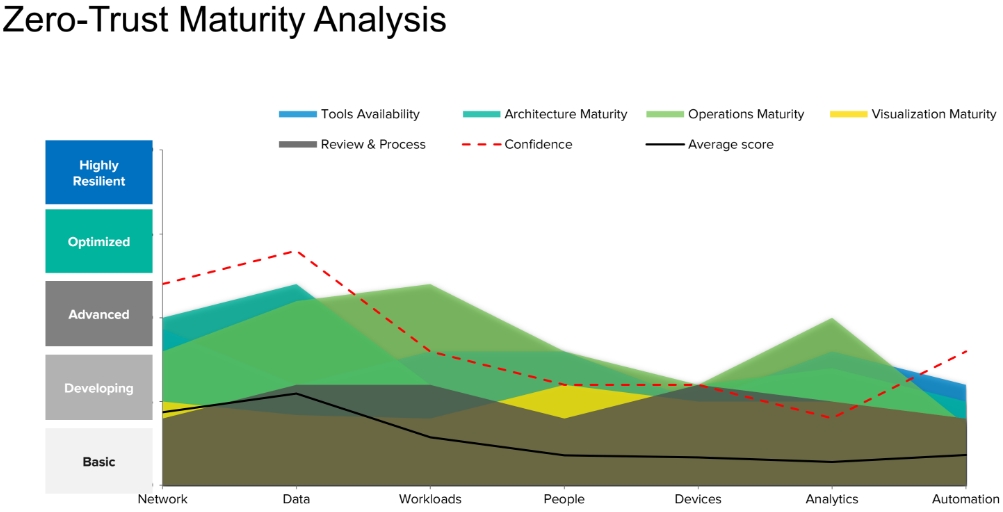
Figure 4: Sample Analysis of Zero-trust Security Maturity
Our assessment reports current zero-trust maturity and defines the direction for a cybersecurity roadmap. Based on this assessment, we prioritize focus areas and align a suite of cybersecurity products and approaches that will address those focus areas. We build use cases related to infrastructure, data and identity, and explore which enhancements, integration mechanisms and orchestrator tools will most effectively address the identified use cases. Finally, we deliver a comprehensive business case for adopting zero-trust, including the expected level of resulting cybersecurity maturity and the business benefits of an improved security posture.
Benefits of a zero-trust framework for banks and financial institutions
Angshuman Chattopadhyay
Infrastructure Security, Zero-trust Security Head within Cybersecurity and Risk Services at Wipro
Angshuman Chattopadhyay is the infrastructure security and zero-trust security leader within Cybersecurity and Risk Services at Wipro. He brings extensive experience with over 21 years in IT and cybersecurity across a wide range of global roles.