Healthcare technology strategy and Internet of Medical Things (IoMT) have become more pertinent than ever. The World Health Organization (WHO) has estimated that there are 2 million different types of medical devices that are categorized into more than 7,000 different generic device groups.
The inter-networked devices in IoMT include medical devices, diagnostic tools, hospital equipment and even wearable tech products. A huge volume of sensitive data is generated and transmitted continuously by the sensors. When vital signs like blood pressure, respiratory rate, pain, level of consciousness, pulse, oxygen saturation etc. are monitored remotely, knowing who has access to it and how it is managed is as important as the data itself. This sensitive data needs to be protected as it progresses through the DIKW (Data, Information, Knowledge, Wisdom) model and throughout the lifecycle from creation through archiving or destruction. One of the viable options to manage this enormous amount of data is to embrace the functionalities offered by secure public cloud platforms. Secure cloud adoption offers several benefits such as analytics capabilities, pre-built HIPAA compliant APIs in addition to meeting unlimited data storage and archival needs.
The Internet of Medical Things (IoMT) is an offshoot of Internet of Things (IoT) and comprises connected healthcare equipment and applications used in medical information technology. The specialized hardware and software components of the integrated OT environments are now a ripe target for threat actors who seek to disrupt operations or steal confidential information.
In Wipro's State of Cybersecurity Report, we analyzed the top 40 publicly reported data breaches and classified the breached data sets into seven broad categories:
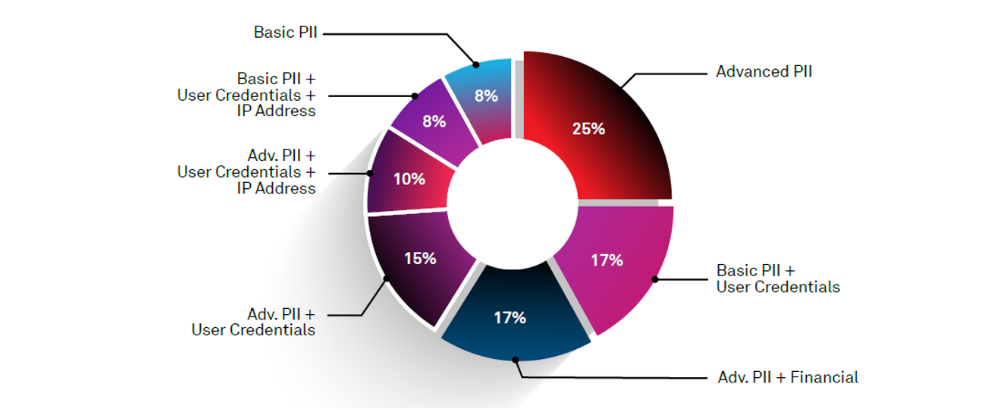
Figure 1: Analysis of compromised data
Wipro’s State of Cybersecurity Report 2020 noted that there has been a universal increase in the deployment of all core organizational control areas. The organizational control deployments for IoT are shown in the Figure 2.
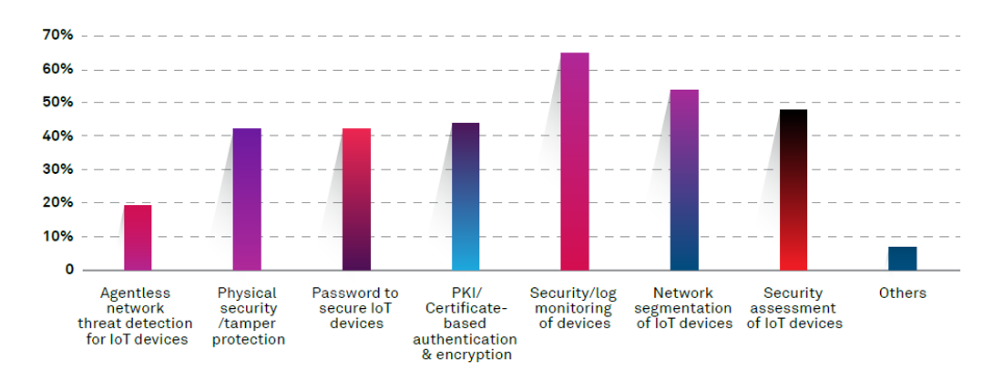
Figure 2: Controls planned to mitigate IoT risks
Healthcare technologies must adopt the cloud to manage the massive scale of devices and healthcare technology improvements. It is imperative that providing a secure and compliant cloud environment forms the baseline for this adoption to be faster and successful.
Leveraging cloud for healthcare requires adherence to Health IT Standards such as C-CDA, HL7, FHIR, DICOM in addition to the standard set of cloud security controls and HIPAA compliance.
Consolidated-Clinical Document Architecture (C-CDA) is a framework for creating clinical documents that contain both human-readable text and machine-readable XML.
Fast Healthcare Interoperability Resource (FHIR) is a specification for exchanging clinical and administrative health care data. The standard is based on REST and OAuth.
Health Level 7 (HL7) v2 messaging is a commonly used data interchange standard. This standard includes messaging specifications for patient administration, orders, results, scheduling, claims management, document management, and many others.
DICOM® is the international standard to transmit, store, retrieve, print, process, and display medical imaging information
Public cloud provides several capabilities to make compliance easier for customers. For example, collaboration tools such as Microsoft Teams, Google Workspace used for telehealth support HIPAA compliance. Customers who are subject to HIPAA must sign a Business Associate Agreement (BAA) with the cloud service provider.
Amazon HealthLake, Amazon Comprehend Medical, Google Cloud Healthcare Data Engine, Healthcare API, and Azure Health Bot are a few examples of purpose-built solutions for the healthcare industry. Leveraging these solutions would significantly enhance the pace of the cloud journey. Readily available tools and templates can be used to build customized healthcare compliant solutions. The cloud environment undergoes multiple independent third-party audits that provide assurance that the implemented controls are validated. For example, adherence to disposal policy and use of techniques described in NIST SP 800-88 Revision 1 “Guidelines for Media Sanitization” is validated during the third-party audit and report on compliance is published.
If tools developed in-house are to be hosted in the public cloud, customers should have the flexibility to access and review logs of action taken by the cloud service provider engineers / administrators. Also, de-identification of data must be done to protect patient privacy. Native security controls should be augmented with cloud security posture management, cloud native security analytics and container security solutions for enhanced protection.
The greatest wealth is health. Health is personal and privacy is key. Privacy by design and privacy by default must be an integral part of every solution. Technologists who develop and implement secure, compliant digital health systems in partnership with health professionals will create enormous value and cybersecurists have a significant role to play.
About the authors
Bhaveshkumar Bhatt
Cloud Security Practice Head at Wipro's Cybersecurity and Risk Services
Bhavesh is the Cloud Security Practice Head at Wipro's Cybersecurity and Risk Services. He is a cybersecurity professional with 21 years of experience in security covering business strategy design, solutions and services development, and program and delivery management across industry verticals.
Allen Stanley Jones
Cloud Security Architect
Allen Stanley Jones is an accomplished Cloud Security Architect with nearly 18 years’ experience in multiple cloud and cybersecurity domains. He has participated in (ISC)² Security Congress and represented Cloud Security in Wipro booth at AWS re:Invent 2018. He is focused on working with clients to ensure that the right guardrails are in place for their fast-paced digital transformation journey.