Companies take different approaches to cloud adoption. While some go all in with a full adoption of cloud infrastructure for applications and services, others move parts of enterprise operations into the cloud. The assumption that applications and data are safe because they are being managed or monitored by cloud providers is wrong. The responsibility of a cloud service provider is only to secure the infrastructure it uses to host its cloud and services.
Companies using the cloud infrastructure are still responsible for ensuring security of their applications and data. As cloud providers offer many types of services, it is a good idea to integrate application security into the cloud migration program.
The state of application security in cloud migration
Worldwide information technology (IT) predictions by the International Data Corporation (IDC) suggest that more than 500 million digital applications and services will be developed and deployed using cloud native approaches by 2023. Many companies have already migrated their applications from the on premise infrastructure to the cloud or are in the process of transferring their applications to the cloud so that they can take advantage of the benefits of cloud computing, including infrastructure as code (IaC), dynamic scaling, and faster time to market.
While companies transition to the cloud, they must consider all aspects of the security posture of their cloud application deployments. It is necessary to perform upfront due diligence when considering data security, secrets, and key management, logging, identity and access management (IDAM), network access and monitoring, and other aspects of cloud architecture, which may vary by cloud provider. However, what about applications’ security? What are the various levels of application security that are performed during re-hosting, refactoring, re-architecting, rebuilding, and replacing? How did the company determine the eligibility of application security during the migration program over the infrastructure as a service (IAAS), platform as a service (PAAS), and software as a service (SAAS) platforms? The dependence on the third party application programming interfaces (APIs) is a major vulnerability; API security controls must match the risk profile of each app.
Building application security controls based on risk
Adoption of a precise application security testing strategy can address the effectiveness of security controls over the modern cloud infrastructure. Many cloud providers offer inbuilt tools to secure defaults on the cloud landscape. However, they lack necessary practical effectiveness due to a lack of strategy to operationalize. It is also necessary for application security measures to be aligned with industry regulations, such as the Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley Act (SOX), Payment Card Industry Data Security Standard (PCI DSS), the National Institute of Standards and Technology (NIST), General Data Protection Regulation (GDPR), and others. Here are a few best practices for app security strategy:
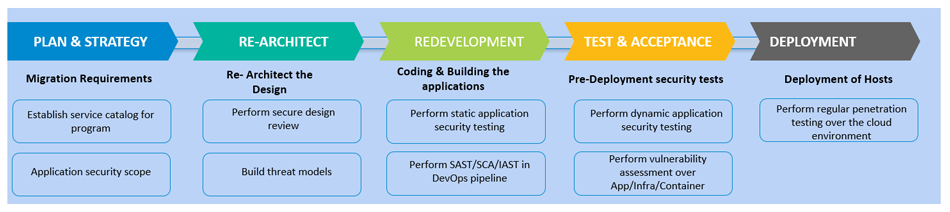
Figure 1: Strategies for securing application migration to the cloud
Securely building and operating applications
Many cloud providers present the option of building, testing, and deploying with continuous integration/continuous deployment (CI/CD) to accelerate software development lifecycle. At the other extreme of the application modernization spectrum, there is a preference for not migrating an existing application, but instead for it to be developed as a “greenfield” or “cloud native” application.
Among the constant challenges facing companies in CI\CD environments is rapid application security testing to ensure speedy production deployment. It may be beneficial for the company to deploy products quickly, but all application security activities have not been performed as a result. The idea is to collaboratively address security throughout the DevOps process as a set of policies, recommendations, and safeguards. Implementation of development, security, and operations (DevSecOps) then becomes a central part of the entire application lifecycle, and every team and person working on an application is required to consider security.
It is very important for an application security strategy to include automation through CI/CD integration and use it to gain an edge over new and evolving threats.
Due to the shift to cloud and cloud-native application technologies, applications are getting more complex. Massively distributed microservices and serverless functions enable developers to focus solely on their own services, and no one has a complete grasp of the entire codebase.
The shift left approach adopted by the company allows developers to analyze code in a GitHub repository to find security vulnerabilities and coding errors in the applications source code or in third party integrated applications. Among the most common security assessments run by DevSecOps operations are static application security testing (SAST), software composition analysis (SCA), interactive application security testing (IAST), dynamic application security testing (DAST), and runtime application self protection (RASP), followed by manual penetration testing.
Many cloud providers include various security tools in their subscriptions, but these tools are not efficient enough to protect against all of the latest cyberattacks. For a secure environment, it is important to follow all the best practices (two factor authentication, strong password, etc.), and to implement a strategy for effective application security.
The cost of modernizing applications over cloud may be costlier if inadequate security practices are followed by companies, but the risk inflates if we do not conduct security assessments at the various phases of cloud migration. Table 1 shows a highly recommended approach to cloud migration.
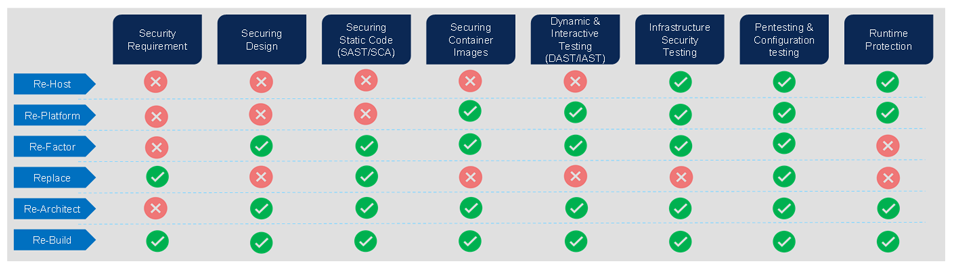
Table 1: Assessments need in cloud migration
Secure way forward
Companies that are moving forward rapidly into cloud applications and infrastructures are required to consider all aspects of security, most notably the role of application security in this program. The mix of technologies and environments used by cloud providers is making them increasingly susceptible to security threats. An effective application security strategy and approach prevents various cyberattacks, meeting the objective of securing the environment of the company. It also makes the cloud migration program economical by conducting security assessment for the cloud migration strategy.
Wipro's Application Security Framework will help your business stay protected and resilient. For more information, contact us at cybersecurity.services@wipro.com .
Industry :

Robin Tiwari
Principal Technical Consultant, Cybersecurity & Risk Services, Wipro
Robin has over 16 years of experience with specialization in the Application security domain. He has worked and managed projects related to Security Architecture, Secure SDLC, Cloud Security, Vulnerability Management, Penetration Testing and Security Solution Designing.
Robin is a Certified Ethical Hacker (CEH) from E-Commerce Consultants International Council. He holds the degree of MS in Cyber Law and Security from the Institute of Management Technology (IMT) Ghaziabad. He also has accreditations with Top 10-security researcher in Q3 2014, Q3 2015, Q4 2015 of the PAYPAL US.

Arun Pillai
DevSecOps Architect, Cybersecurity & Risk Services, Wipro
Arun champions DevSecOps charter for Security Assurance Service within Wipro's Cybersecurity and Risk Services division. He has over 14 years of experience with specialization in the security domain. He has worked and managed projects related to Security Architecture, Secure SDLC, Threat Modelling, Secure Coding, Penetration Testing and Security Consulting.
Arun is an ISC2 Certified Information Systems Security Professional (CISSP) and ISACA's Certified in Risk and Information Systems Control (CRISC). He holds a Master's degree in Information Technology from Sikkim Manipal University of Science & Technology and is a TOGAF certified Enterprise Architect from TheOpenGroup.