In just two months, between January and March of this year, usage of virtual private networks (VPNs) and remote desktop protocols (RDPs) increased 124% and 41%respectively in North America.
Businesses have shifted to remote work fast – but are they aware of the risks associated with this new paradigm?
An OpenVPN survey reports that 73% of executives “believe remote workers pose a greater risk than onsite employees.”
Remote workforces require enhanced security controls. New applications and infrastructure changes that allow employees to work from home also increase an organization’s exposure to cyber threats.
As businesses move quickly to cloud-based solutions that support remote work, many are neglecting their security architecture and the necessary monitors and protocols, leaving them more vulnerable than ever to the rising number of cyberattacks.
Named as a leader in Everest Group’s 2020 PEAK Matrix Assessment for IT security services providers, Wipro is well positioned to help you achieve cyber resilience while transitioning to new ways of working. Here, we’ll get you started by guiding you through the first steps toward cybersecurity preparedness.
How sound is your
security architecture?
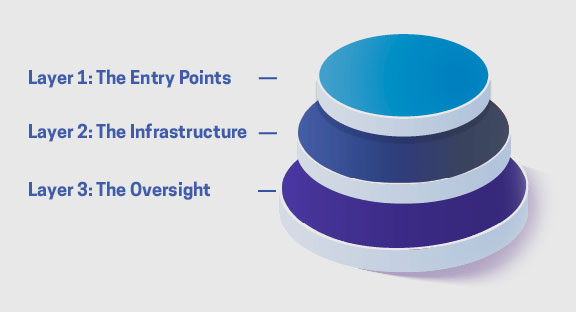
To answer this question, CISOs need to consider their organizations’ cybersecurity across all touchpoints: from highcontact entry points to essential infrastructure to monitoring and oversight.
Information leaks
Accessing company data from a home or pubic network puts sensitive information at risk.
Vulnerable Devices
Unlike workstations and devices managed by the organization, personal devices may not meet company security standards, or be equipped with the necessary monitors or controls.
Supply chain disruptions
Visibility throughout your supply chain is essential for continuity planning as well as security planning. To stay ahead of disruptions, businesses need to be able to identify threats all along the pipeline.
Exposure to threats
Network changes, new VPN configurations, alternate devices, ports, and IP addresses: transitioning to new operations can leave your organization temporarily exposed and more vulnerable to cyber threats.
Regulation oversight
How well do your existing security regulations apply to remote work? Unless you’re reviewing and renewing them, it’s hard to say for sure. Remote work presents new scenarios and applications that may not be accounted for in traditional regulations, resulting in security oversights.
Human errors
Quick shifts to new processes with little notice increase the chance of people making mistakes. Without proper training, workers may not be aware of security best practices, inadvertently putting the organization at risk.
Limited system capabilities
How many VPN connections will your remote workforce require? How many can your IT infrastructure support? Not knowing your system’s capabilities can doom your shift to remote work before it even begins.
Identity threats
Identity theft has always been a big threat to cybersecurity, and remote connections elevate the risk. Insufficient access monitoring (least privilege standards, gated controls) and weak authentication processes for third-party applications (cloud, SaaS) open the doors to fraudulent activity. Still, many organizations lack adequate endpoint controls for remote work. Hackers know this, and they’re exploiting these weaknesses, flooding organizations with digital identity threats.
1. Comprehensive risk assesment
Evaluate your security architecture and any planned changes to support your cloud-based or remote-friendly workforce. We put together a free WFH self-assessment to get you started. It’s based on frequently asked questions from enterprise clients about their own work-from-home programs. These questions will test your familiarity of the risks associated with working from home, how prepared you are to mitigate them, and guide you toward a more efficient cybersecurity preparedness plan.
2. Robust strategy
Focus on filling any gaps in your security system and reinforcing potential weaknesses.
At Wipro, we divide our response-planning into several targeted scenarios to be sure we fully cover all aspects of the cybersecurity ecosystem. Common response scenarios for cybersecurity include:
• Remote access and computing
• Privileged access and operations
• SaaS adoption for short-term business continuity plans
• Multi-factor authentication for enterprise
• Supply chain continuity and capacity
3. Concerted, impactful action
With a holistic approach, you’ll balance short-term and long-term objectives