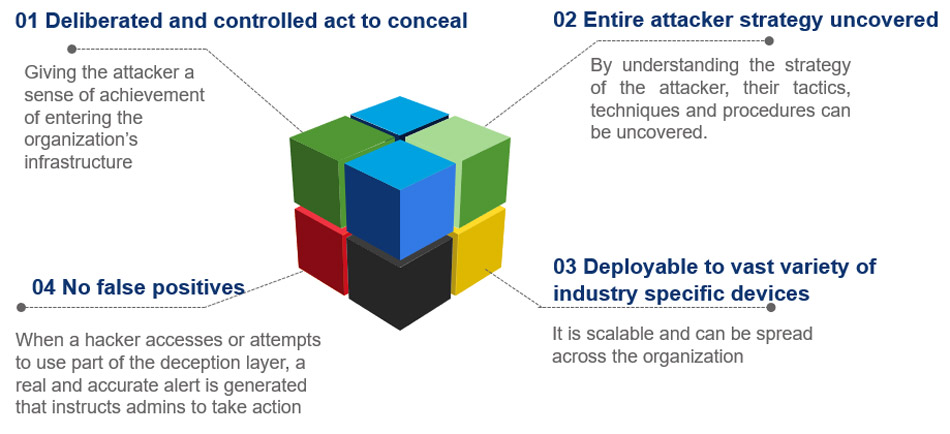
A comprehensive defense strategy that leverages deception to swiftly thwart sophisticated zero day attacks.
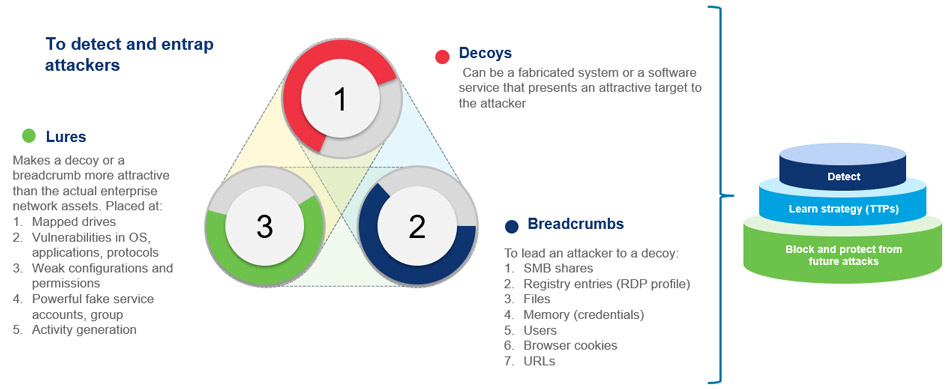
Cyber deception has emerged as an effective and offensive threat hunting technology to offer protection for core information networks and infrastructure. It involves luring attackers to decoy systems, which unmasks their activities and provides key indicators of compromise. This enables defenders to act swiftly and thwart sophisticated zero day attacks. The technology also gives attackers a false sense of achievement by allowing them to believe that they have penetrated the network. Deception technology can be placed across enterprise networks by placing decoys, breadcrumbs and lures.
It empowers organizations with a proactive defense strategy by providing comprehensive coverage on zero-day exploits. It also reduces the dwell time of the intruder from over 180 days to a few hours, providing maximum accuracy (high fidelity detection) with minimal human intervention.
Wipro’s AI-based deception technology can be integrated with SIEM, EDR and firewalls to provide a more holistic picture of the attack surface. Once there is positive affirmation of a compromise (on a decoy), a “Detect and Deflect” approach will elect to block the threat actor. Advanced IR (incidence response) and threat hunting capabilities provide us the opportunity to engage with the attacker and learn more about the threat actor’s TTP (tools, techniques and procedures). Wipro facilitates seamless integration with other detective and protective security controls to enhance layered defenses. We partner with Acalvio to offer Managed Deception Services to our customers.