Introduction
Cyber-attack threats are on the rise, and the cost of Cybercrime continues to increase in the financial services industry. In the next five years, Cybercrime cost is expected to increase by 40%. Although large-scale cyber-attacks have occurred over the past 15 years in the form of distributed denial of service, data theft, loss of intellectual property, and cyber fraud, their impact has grown faster than the firm’s ability to prevent and recover from it. Usually, organizations focus on external threats, but insiders are often more likely to be the cyber-attack source in Capital Markets. One of the largest global bank recently faced a loss of $900 million due to an insider breach; this is testimony to the fact that internal cyber-attacks are more common than many assume.
Humans are the weakest link in cybersecurity. Employee negligence and lack of awareness remain to be the top threats for Capital Market firms as far as cyber risk is concerned. A Gartner study on criminal insider threats found that 62% of insiders with malicious intent are classified as people who are looking for extra financial gain. 14% of malicious insiders were in a leadership role, and around 1/3rd had access to sensitive information.
As per Wipro’s State of Cybersecurity Report (SOCR) - The top cyber risks that financial services organizations face today are:
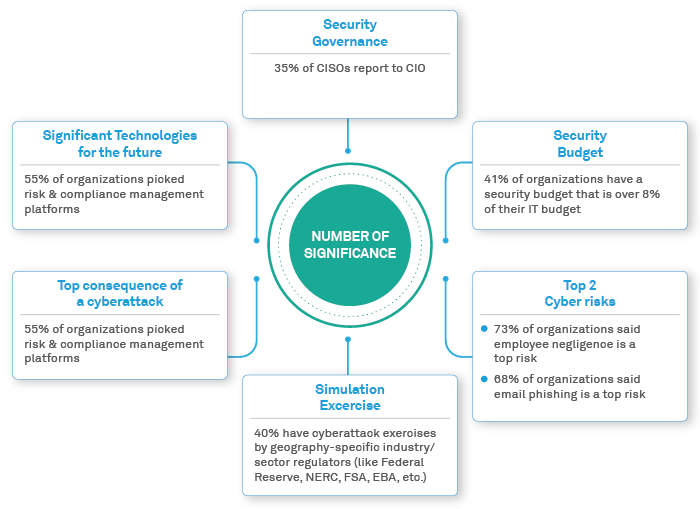
Figure 1: State of Cybersecurity Report
Insider threat - the human factor contributing to cyber and operational risk
Capital Market firms trust their employees, vendors, and contractors with valuable data, including confidential client information, which eventually increases the risk of an insider attack. Insider threats are considered highly dangerous as it is difficult to predict and detect such threats timely; this ultimately results in the rise of the overall cost of insider threats. Such attacks occasionally occur through negligence on the part of employees, or when an employee has malicious intentions leading to deliberate sabotage.
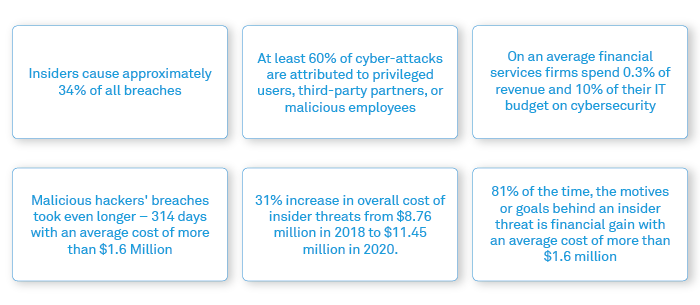
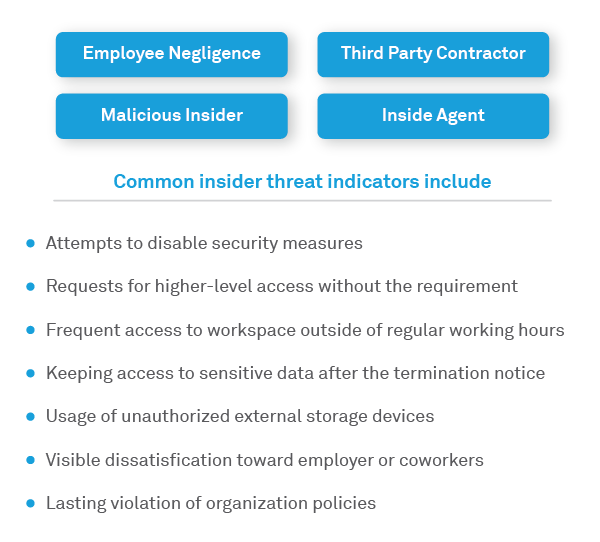
Figure 2: Insider threat Indicators
A view on Insider Threats applicability to the Capital Markets value chain
Capital Market firms are possible targets for attackers for several reasons. Firstly, they handle a wealth of customer financial data. Secondly, they own valuable intellectual property around investment strategies and trading algorithms. Insider threats can significantly harm organizations' operational resilience, financial status, and reputation as they have access to sensitive information, critical applications, and systems.
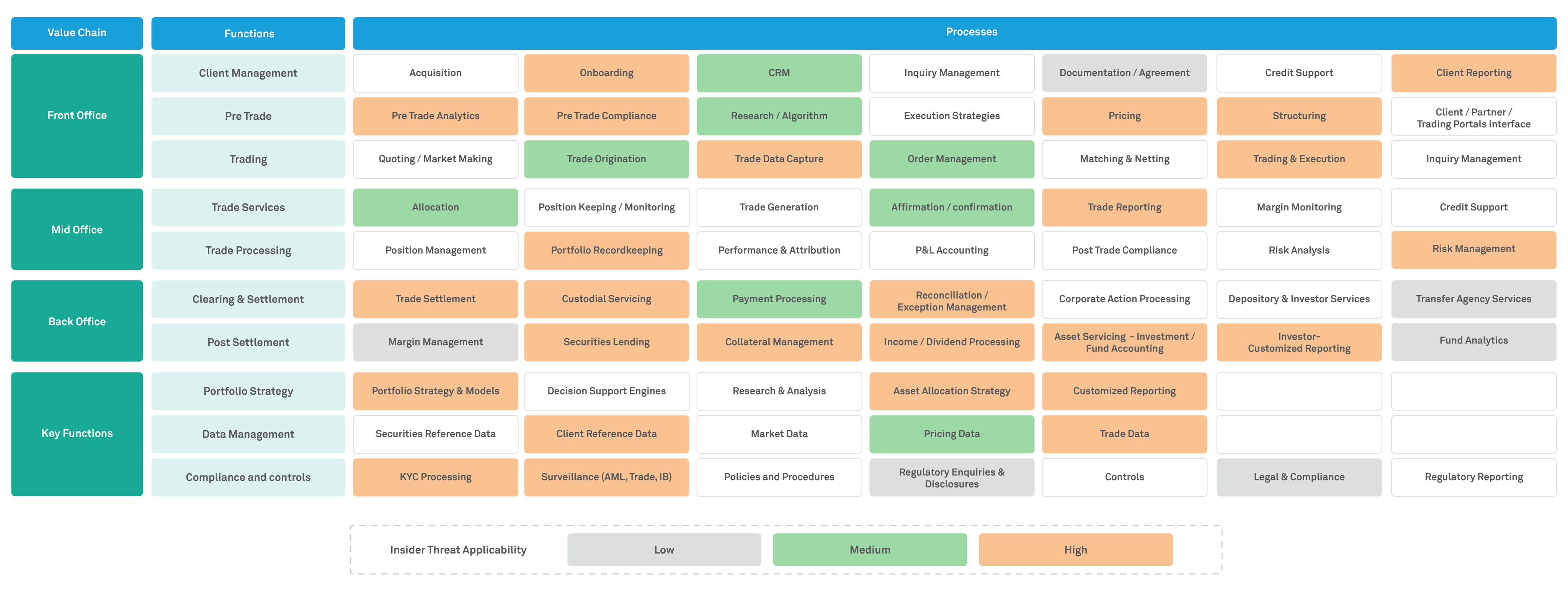
Figure 3: Capital Markets value chain
The potential risks posed by insider threats within the Capital Markets include:
The impact of Insider Threat is pervasive across Capital Markets. Organizations are required to keep up with the regulations and protect sensitive data. On the other hand, they must adapt to digital technologies, which raises the risk of cyber-attacks due to increased online presence, more extensive use of social media, and mass adoption of mobile devices. This is further amplified in the current COVID environment with increased Work from Home (WFH) and higher digital channel usage. Cyber-risk issues are becoming more costly to address, and any reputational issue has a lasting impact on customer trust and retention. Regulators demand a much greater level of monitoring and awareness at all levels, with a more comprehensive approach to achieve cyber resilience by including human aspects in addition to technology solutions.
Building a cyber-resilient ecosystem - Holistic approach toward insider threats protection
Insider threats are ongoing, and in today's scenario, it's one of the major threats across Capital Market firms. Insider-threat incidents are caused by a combination of technical, behavioral, and organizational factors. As a result, effective management requires a disciplined, risk-based, cross-functional approach that includes corporate security, information security, legal, Human Resources (HR), audit, and other relevant control functions. The attacks faced nowadays are dynamic, so firms' cybersecurity approaches should also be evolved continuously.
To achieve cyber resiliency in principle, firms should take a holistic approach by focusing on:
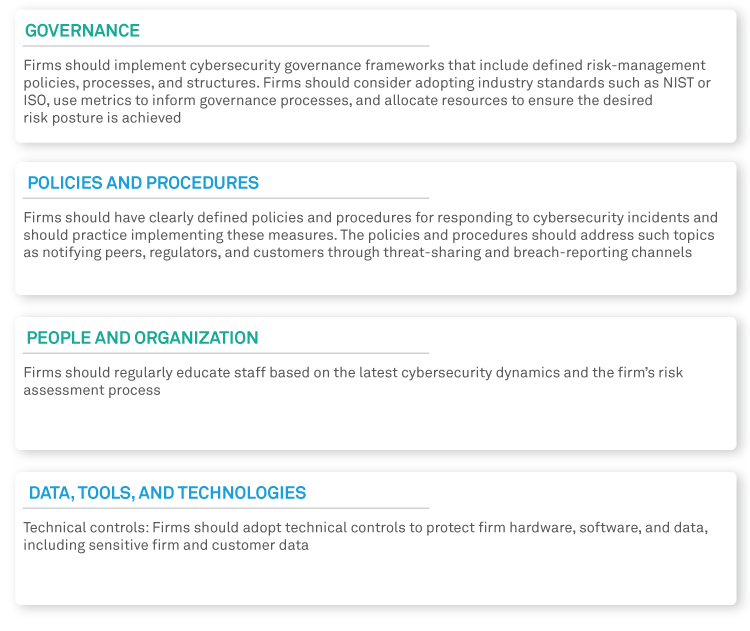
Figure 4: Key focus areas to build holistic approach
Insider threats Protection – Approach and technology perspective
A holistic approach is mandatory for efficient and effective cyber-risk management. Ultimately, organizations will have to integrate business, operations, security, and risk teams for efficient intelligence-sharing and collaborative responses to insider threats. Industry standards, guidelines, and frameworks serve as guidance for firms to implement a cybersecurity strategy. Standards like the National Institute of Standards and Technology (NIST) represent a well-defined core framework consisting of core functions to establish a defense strategy.
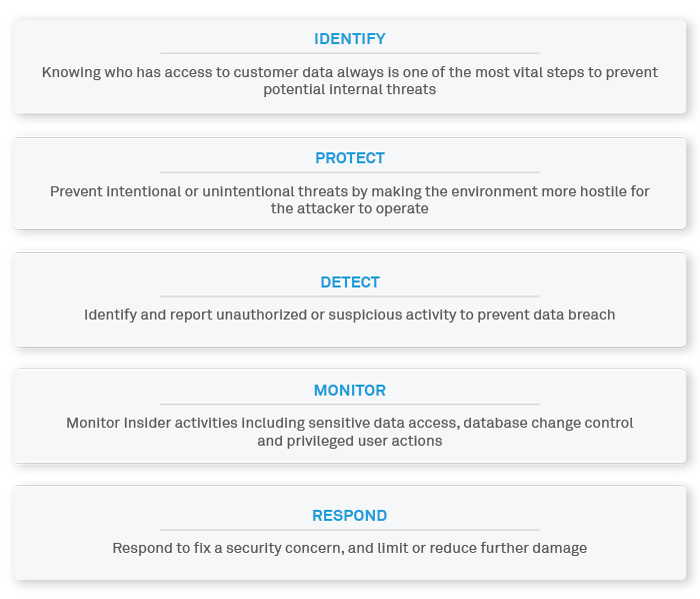
Build a holistic and robust environment
There are many tools and technologies for insider-threat protection, which includes data governance, identity access management and control, asset classification, encryption, and data loss prevention.
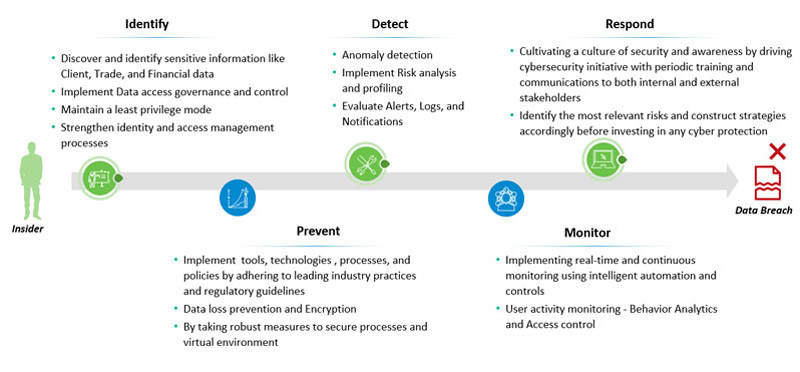
Figure 5: Insider Threats Approach
It’s critical that Capital Market firms build a comprehensive insider-threat approach. An effective way to handle such threats is to empower network monitoring solutions, such as data loss prevention (DLP) policies at endpoints to prevent data exfiltration and support remote compliance with data-protection legislation by applying policies to sensitive data directly. Secondly, firms should monitor user activity and behavior by implementing user and entity behavior analytics (UEBA)
With the rise in the frequency, severity, and sophistication of cyber-incidents, various regulatory and supervisory actions are taken to increase cyber resilience. Regulators expect firms to develop "secure by design" systems, focusing on resilience to insider threats rather than focusing on compliance with a standard checklist. In recent years, regulators and industry associations have made a rigorous effort to improve the Capital Market cybersecurity and cyber-resilience capabilities. Here are few regulations that define guidelines and best practices to comply with, in the event of a cybersecurity incident.
Capital Market firms cannot overlook cybersecurity and its implications. It’s important to make sure that firms operate securely in this digital world. To build an insider threat program, all stakeholders should collaborate to identify critical assets, risk indicators, relevant data sources, compliance requirements, cultural concerns, and privacy implications. The very first step a firm can take is to implement Data Access Governance (DAG) to stop any insider threat. With DAG in place, firms can identify and discover sensitive data and limit access to authorized users only. It is also necessary to articulate explicitly and without ambiguity the roles and responsibilities of board members, senior management, and other vital positions to define right access. Firms need to be proactive and should continue working with regulators to build a cyber-resilient ecosystem that focuses on strengthening their cybersecurity strategy.
References
https://www.nist.gov/cyberframework
https://www.sifma.org/resources/general/best-practices-for-insider-threats/
https://www.pwc.com/us/en/services/alliances/microsoft-business-applications/insider-risk-management.html
https://www.itgovernance.co.uk/cyber-resilience
https://blog.rsisecurity.com/cyber-security-resilience-framework-how-to-get-started/
https://thycotic.com/company/blog/2020/05/12/insider-threats-in-cyber-security/
Anamika Sharma
Solution Design Lead - Capital Markets
Anamika is a solution design lead in the Capital Markets vertical at Wipro. She has over 17 years of experience spanning program management, solution development, consulting, and sales strategy. Anamika has a deep understanding of technology and has been instrumental in developing relevant solutions/response designs for technology proposals in the financial services domain. You can reach her at anamika.sharma8@wipro.com